Berikut ini kita berbagi Peralatan / Tools yang biasanya dipakai oleh pentester, hacker, cracker, phiser dan bahkan Anonymous. Anonymous Hacking Tools 2013 – 2014, Anonymous Cracking Tools 2013 -2014. Download Hacking Tools 2013 – 2014, Phising Tools 2013 – 2014, Hacking Tools 2013 – 2014, Tools Hacking 2013 – 2014, Cracking Tools 2013 – 2014, Tools Cracking 2013 – 2014, Tool Hack 2013 – 2014, Tool Crack 2013 – 2014, Tool Hacking 2013 – 2014, Tool Cracking 2013 – 2014, Tool Hacker 2013 – 2014,Tool Cracker 2013 – 2014, Tools Hacker 2013 – 2014, Tools Cracker 2013 – 2014 yang mungkin bisa bermanfaat untuk bisa anda pakai di 2013 – 2014.
Ayo Download Hacking Tools 2013 – 2014 – Hacker Tools 2013 – 2014 – Hack Tool 2013 – 2014 – Hacker Tool 2013 – 2014 – Hacking Tool 2013 – 2014 – Hack Tool 2013 – 2014 – Cracking Tools 2013 – 2014 – Cracker Tools 2013 – 2014 – Cracking Tool 2013 – 2014 – Cracker Tool 2013 – 2014 – Crack Tools 2013 – 2014 – Crack Tool 2013 – 2014.
Happy Hacking & Cracking All:
1. [JBRUTE V0.9.4] OPEN SOURCE SECURITY TOOL
JBrute adalah aplikasi open source yang ditulis menggunakan Java untuk mengaudit keamanan dan password yang disimpan didalam system, bisa digunakan untuk aplikasi open source dan aplikasi komersial. Difokuskan untuk menyediakan dukungan multi-platform dan parameter fleksibel untuk kebutuhan skenario pengecekan.
Requirement: Java Runtime version 1.7 or higher.
Fitur-fitur yang tersedia:
- Muli-platform support (by Java VM)
- Several hashing algorithms supported
- Flexible chained hashes decryption (like MD5(SHA1(MD5())))
- Both brute force and dictionary decryption methods supported
- Build-In rule pre-processor for dictionary decryption
- Multi-threading support for brute force decryption
Supported algorithms:
- MD5
- MD4
- SHA-256
- SHA-512
- MD5CRYPT
- SHA1
- ORACLE-10G
- ORACLE-11G
- NTLM
- LM
- MSSQL-2000
- MSSQL-2005
- MSSQL-2012
- MYSQL-322
- MYSQL-411
- POSTGRESQL
- SYBASE-ASE1502
2. [ARACHNI V0.4.5.1-0.4.2] OPEN SOURCE WEB APPSEC SCANNER
Arachni adalah aplikasi gratis (Open Source project) untuk mencari kelemahan dan mendukung keamanan aplikasi, release code dibawah Apache License Version 2.0 dan kita semua gratis menggunakannya.
Fitur-Fitur dan Perubahan yang tersedia:
- Optimized pattern matching to use less resources by grouping patterns to only be matched against the per-platform payloads. Bottom line, pattern matching operations have been greatly reduced overall andvulnerabilities can be used to fingerprint the remote platform.
- Modules
- Path traversal ( path_traversal)
- Updated to use more generic signatures.
- Added dot-truncation for MS Windows payloads.
- Moved non-traversal payloads to the file_inclusion module.
- File inclusion ( file_inclusion) — Extracted from path_traversal.
- Uses common server-side files and errors to identify issues.
- SQL Injection ( sqli) — Added support for the following databases:
- Firebird
- SAP Max DB
- Sybase
- Frontbase
- IngresDB
- HSQLDB
- MS Access
- localstart_asp — Checks if localstart.asp is accessible.
- Path traversal ( path_traversal)
- Plugins — Added:
- Uncommon headers ( uncommon_headers) — Logs uncommon headers.
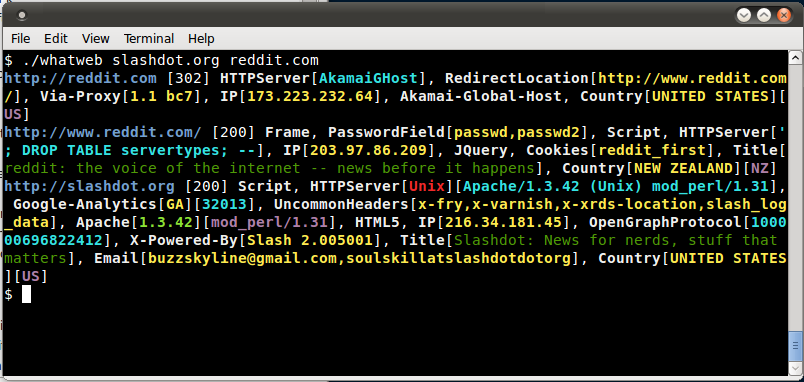
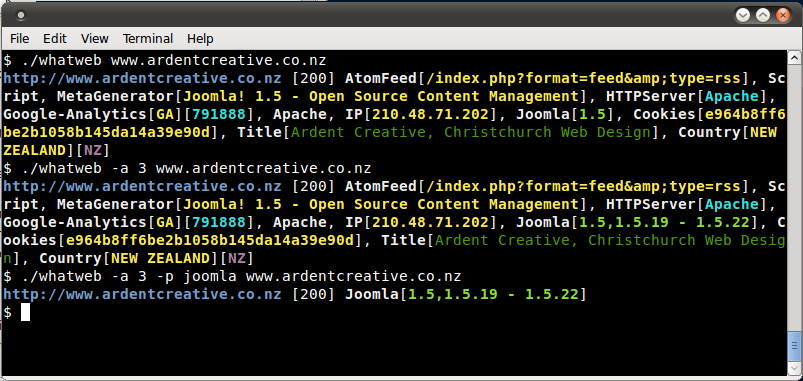
3. [WHATWEB V0.4.7] CMS TECHNOLOGY SCANNER
WhatWeb digunakan untuk mengidentifikasi websites. Tujuannya adalah untuk menjawab pertanyaan, “What is that Website?”. Detail website akan diberikan sesuai dengan kebutuhan. Biasanya digunakan untuk Content Management System seperti “WordPress, Joomla, dsb”.
Fitur-fitur yang tersedia:
* Over 900 plugins
* Control the trade off between speed/stealth and reliability
* Plugins include example URLs
* Performance tuning. Control how many websites to scan concurrently.
* Multiple log formats: Brief (greppable), Verbose (human readable), XML, JSON, MagicTree, RubyObject, MongoDB.
* Recursive web spidering
* Proxy support including TOR
* Custom HTTP headers
* Basic HTTP authentication
* Control over webpage redirection
* Nmap-style IP ranges
* Fuzzy matching
* Result certainty awareness
* Custom plugins defined on the command line
* Over 900 plugins
* Control the trade off between speed/stealth and reliability
* Plugins include example URLs
* Performance tuning. Control how many websites to scan concurrently.
* Multiple log formats: Brief (greppable), Verbose (human readable), XML, JSON, MagicTree, RubyObject, MongoDB.
* Recursive web spidering
* Proxy support including TOR
* Custom HTTP headers
* Basic HTTP authentication
* Control over webpage redirection
* Nmap-style IP ranges
* Fuzzy matching
* Result certainty awareness
* Custom plugins defined on the command line
Contoh penggunaan:
Check beberapa website:
Menggunakan fitur untuk mencari informasi yang lebih detail.
4. [JSQL INJECTION V0.5] JAVA TOOL FOR AUTOMATIC DATABASE INJECTION
jSQL Injection adalah aplikasi yang ringan untuk mendapatkan informasi database dan mengexploitasi database.
jSQL free, open source and cross-platform (Windows, Linux, Mac OS X, Solaris).
Fitur- Fitur jSQL Injection – Versi 0.5:
- SQL shell
- Uploader
- Admin page checker and preview
- Brute forcer (md5 mysql)
- Coder (encode decode base64 hex md5)
- Distant file reading
- Webshell deposit
- Terminal for webshell commands
- Configuration backup
- Update checker
- Time based algorithm
- Multi-thread control (start/pause/resume/stop)
- Shows URL calls
- GET, POST, header, cookie methods
- Normal, error based, blind algorithms
- Automatic best algorithm selection
- Progression bars
- Simple evasion
- Proxy setting
- Supports MySQL
5. [SPEARPHISHER] A SIMPLE PHISHING EMAIL GENERATION TOOL
SpearPhisher adalah sebuah tools yang digunakan untuk menyebarkan halaman phising. Tools ini sangat mudah digunakan dan sangat powerfull untuk kegiatan phising.
Fitur-Fitur yang tersedia:
- The tool supports specifying different sending names and email addresses, multiple recipients via TO, CC, BCC, and allows bulk loading with one recipient email address per line in a file.
- It allows customization of the subject, adding one attachment, and SSL support for SMTP enabled mail servers. One of the popular features with our client is the WYSIWYG HTML editor that allows virtually anyone to use the tool; previewing results as you point and click edit your malicious email body.
- If you want to add custom XSS exploits, client side attacks, or other payloads such as a Java Applet code generated by the Social Engineer Toolkit (SET), its split screen editor allows more advanced users to edit HTML directly.
6. [COOKIECATCHER] SESSION HIJACKING TOOL
Fitur-fitur yang tersedia:
- Prebuilt payloads to steal cookie data
- Just copy and paste payload into a XSS vulnerability
- Will send email notification when new cookies are stolen
- Will attempt to refresh cookies every 3 minutes to avoid inactivity timeouts
- Provides full HTTP requests to hijack sessions through a proxy (BuRP, etc)
- Will attempt to load a preview when viewing the cookie data
- PAYLOADS
- Basic AJAX Attack
- HTTPONLY evasion for Apache CVE-20120053
- More to come
- Prebuilt payloads to steal cookie data
- Just copy and paste payload into a XSS vulnerability
- Will send email notification when new cookies are stolen
- Will attempt to refresh cookies every 3 minutes to avoid inactivity timeouts
- Provides full HTTP requests to hijack sessions through a proxy (BuRP, etc)
- Will attempt to load a preview when viewing the cookie data
- PAYLOADS
- Basic AJAX Attack
- HTTPONLY evasion for Apache CVE-20120053
- More to come
Video Demo: http://www.youtube.com/watch?v=2GH6RRozOpY
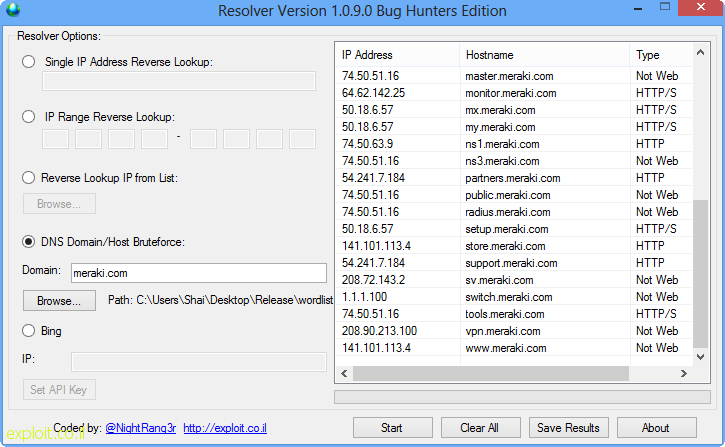
7. [RESOLVER V1.0.9] THE REVERSE/BRUTEFORCE DNS LOOKUP
Fitur-fitur yang tersedia:
- Resolve a Single IP
- Resolve an IP Range
- Resolve IP’s provided in a text file
- Export Results to a text file
- Copy results to Clipboard
- DNS Records brute force
8. [RAFT V3.0.1] RESPONSE ANALYSIS AND FURTHER TESTING TOOL
RAFT adalah testing tool untuk mengidentifikasi kelemahan terhadap aplikasi web.
9. [DROIDSQLI] MYSQL INJECTION TOOL FOR ANDROID
DroidSQLi adalah untuk melakukan SQL injecttion dengan menggunakan perangkat Android.
Fitur-fitur yang tersedia DroidSQLi:
- Time based injection
- Blind injection
- Error based injection
– Normal injection
Download DroidSQLi

- Time based injection
- Blind injection
- Error based injection
– Normal injection
Download DroidSQLi

10 [RIPS] A STATIC SOURCE CODE ANALYSER PHP
RIPS adalah tools yang dibuat menggunakan PHP untuk menemukan kelemahan pada aplikasi yang berbasis PHP dengan metode static code analysis.
Fitur-fitur yang tersedia:
- Code Execution
- Command Execution
- Cross-Site Scripting
- Header Injection
- File Disclosure
- File Inclusion
- File Manipulation
- LDAP Injection
- SQL Injection
- Unserialize with POP
- XPath Injection
- … other
Code audit interface
- scan and vulnerability statistics
- grouped vulnerable code lines (bottom up or top down)
- vulnerability description with example code, PoC, patch
- exploit creator
- file list and graph (connected by includes)
- function list and graph (connected by calls)
- userinput list (application parameters)
- source code viewer with highlighting
- active jumping between function calls
- search through code by regular expression
- 8 syntax highlighting designs
- … much more
Static code analysis
- fast
- tokenizing with PHP tokenizer extension
- taint analysis for 232 sensitive sinks
- inter- and intraprocedural analysis
- handles very PHP-specific behaviour
- handles user-defined securing
- reconstruct file inclusions
- detect blind/non-blind exploitation
- detect backdoors
- 5 verbosity levels
- over 100 testcases
- … much more
Selamat mempelajari, mencoba dan menggunakan. Gunakanlah sesuai dengan sebaik-baiknya dan sesuai kebutuhan 
















0 komentar:
Posting Komentar